 Almost a year passed since my experimental “honeypot” post on the spam received on my blog. As I then decided, I let all spam comments through, that were not captured by the Spam Karma. I did this about 3-4 times in the passed months, as I don’t spend much time on the administration interface. Based on an emerging pattern I observed I then started to do this more frequently in the recent weeks.
Almost a year passed since my experimental “honeypot” post on the spam received on my blog. As I then decided, I let all spam comments through, that were not captured by the Spam Karma. I did this about 3-4 times in the passed months, as I don’t spend much time on the administration interface. Based on an emerging pattern I observed I then started to do this more frequently in the recent weeks.
When I wasn’t “active” on approving spam, first it started to calm down, and less-and less spam arrived each day. The other posts have not received more spam than 2-3 in the entire year, while this one had spam coming in every now-and-then.
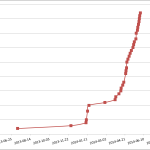
When I approved some of the cumulated comments in January, I have received several new comments shortly. Then came a long silence, when I didn’t approve anything. On the graph you can see how I started to receive the tons of spam, when I decided to approve more frequently.
It’s interesting to notice, that the spambots report to use Internet Explorer 6.0 on Windows XP exclusively, with a number of small variations in the signature. They are all using fake gmail addresses. The content of their posts is diverse in both the way they operate and the content they link to. They are never coming from the same IP address twice. I suspect they are created using various botnets.
It’s almost certain the feedback of the posts in the gmail boxes are monitored by the authors, and the targets are “whitelisted” to receive more spam. Also it seems, that this kind of monitoring only works until a certain amount of time, thus if the approval is late, there is no effect. Probably these accounts are already abandoned and hopefully destroyed by Google.
This experiment was neither scientific, neither through, it was only performed to satisfy my curiosity of how, my otherwise rarely visited site gets peaks of attention.
I can draw two conclusions from this. There are still massive botnets out there handing out spam at a furious pace. There can not be a certainty about easily faked browser signatures, but I suspect they really run on the ever so vulnerable XP-s. The other is, that s long as there are people to pay for this form of useless advertising/SEO, there will be massive cyber attacks, spams, and botnets.
I’m closing my previous post for comments, so the “return customers” would not spam it anymore. 🙂